 |
| Underwater Drone For Surveillance - Architecture |
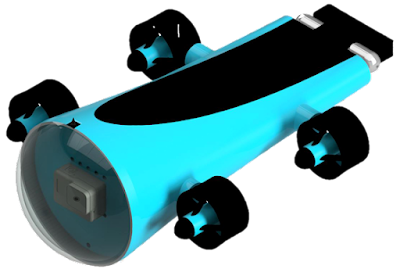
INTRODUCTION
Underwater drone
is a smart device with the use of sensors in lower cost to capture the beauty
of a small pound and gather it from different angle, which human eye is unable
to see.
FEATURES
Drone is
extremely easy to operate due to its internal design and it has multiple
protections which a drone can face under the water in normal conditions. The
drone has the ability to provide a live feed and its smart structure makes it
to operate in 360 degree and also give the life feed to screen.
CAMERA
There is a glass
in front of the drone from where a camera is installed which helps to monitor
the live view under the water without effecting from water. The glass also
helps to cut through the water.
Smart Balancing
The drone has a smart balancing system to itself. The sensor automatically operates the engine
without affecting anything and keeps it at a specific angle in all three
directions.
Object Detection
The drone can
have protection from obstacles. In case of any object in front or beneath
the done, it stops the engine to move in that direction.
Waterproof
The whole
operating system is made of electrical and it is difficult to operate these
appliances underwater. In drones most of the sensors are waterproof but the
rest of the design uses the sealing in the body to avoid water interaction with the internal system.
VISUAL
 |
| Underwater Drone For Surveillance - Architecture |
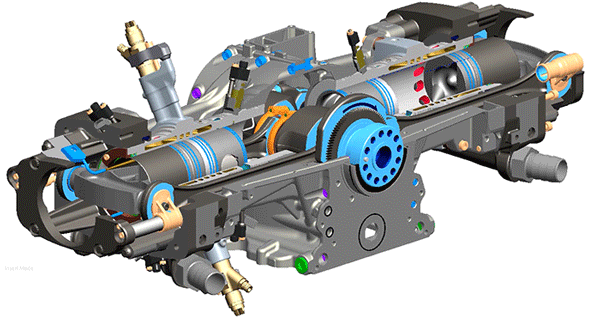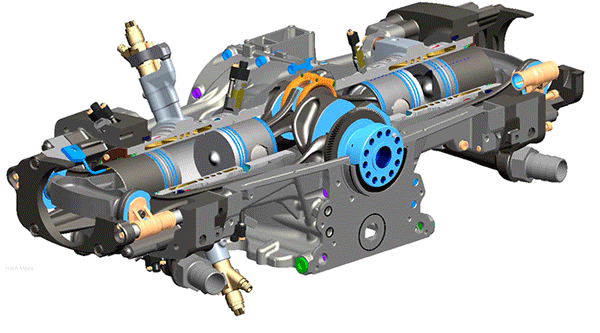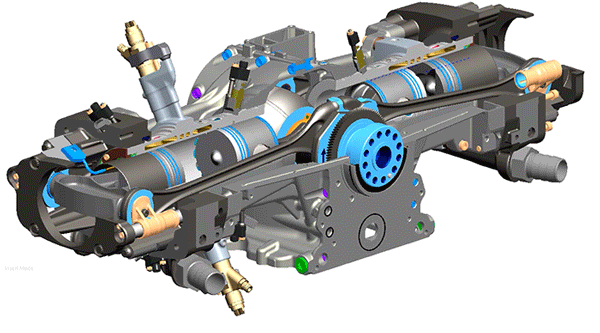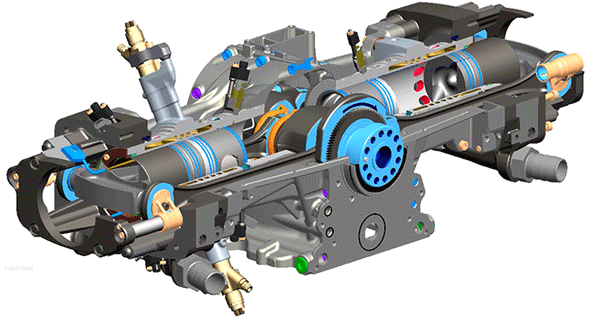
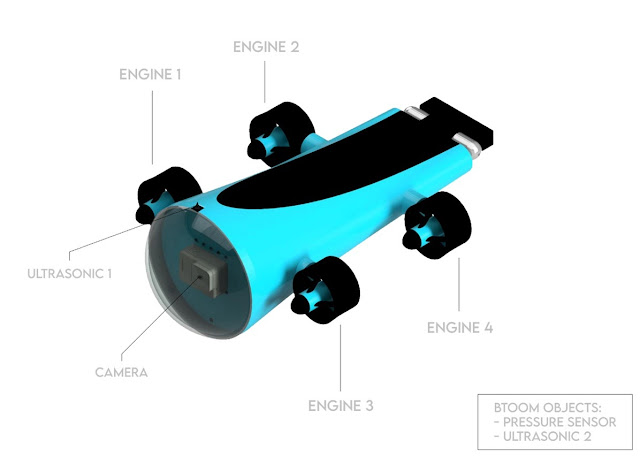
Detail
The features of
drones may be limited but their internal design requires special attention. The
internal structure is a combination of different devices, most of them are
seniors and their spatiality is that they all fit for their role with the
drone. As you can see in the image, we have multiple sensors but some of them
are hidden inside. Let me describe what each device does in the drone.
Motors
 |
| FANS |
In
the drone, there is only one major CPU that controls all the functionality. The
drone processor uses timely loops to control the motors and sensors keep
running in the background to provide the continuous signal. The main drone
functions are its movement. To make the drone moveable, waterproof motors have
been used. The motors are attached to further fans and servo motors. The
combination of servo and other motors helps it to move in all directions without
any issue. The motors use a driver which makes the motors move in both
directions on the basis of the incoming signals.
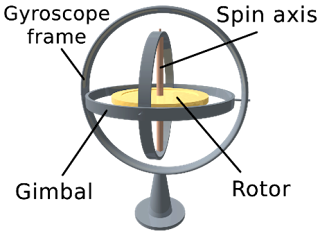
Gyroscope
The motor
movement receives from remote which uses sound waves to send a signal but the
problem here is a little different. When the remote sends the signals to the drone
then its motors start operating as it has been set on different signals. The
problem here is the drone direction can also affect water flow. To avoid
the effect of water on drone movement a gyroscope sensor has been used to
control that. The sensor keeps the drone at a specific angle. Every time the
drone losses its position by water flow, the sensor makes the motors move it
back to its specific point. The basic function of the gyroscope is to tell all of
its angles in all 3d planes. The smart programming helps to automatically operate
the motors in case of a change in angle from a specific point.
 |
| Gyroscope |
Camera Feedback
The camera part
is one of the most amazing parts of the drone due to its calculated design. The
camera is hidden behind the glass, from which it takes a full front view. The
glass protects the camera from water and its curvedness makes it cut through
the water. That flow of drones has a much lower effect on drones’ motors. The
camera captures the beautiful movements underwater and sends them to the surface
where it is canalized to the screen which is set on the remote. The live view of the screen can control the drone
but there Is a little bit of latency issue in the whole process. The
millisecond's difference puts the drone in a risky state. This problem is solved
by some other sensors.
Ultrasonic Sensors
There are two
waterproof ultrasonic sensors attached to the drone. The one is on the head of
the drone which checks the obstacle in the front direction and the other one is
attached beneath the drone. It checks the obstacle under the drone. Both
sensors help to avoid obstacles in case a user is unable to view on the screen.
Both of these sensors are waterproof and specially designed to operate
underwater. Besides these sensors, there are some others, especially in the drone.
There are other two sensors that help to decide the underwater environment.
 |
| Sensor |
Temperature Sensor
The temperature
sensor helps to avoid the high and low temperature issue. The temperature
sensor it helpful when an animal is near to the drone. It can calculate the
water temperature. The temperature sensor only helpful in close interaction of
an animal but the other sensor known as pressure sensor solve the other issue.
Pressure Sensor
The pressure
sensor helps to calculate the pressure of the water. In case of water pressure
changes then it can be received by the pressure sensor. The pressure sensor has
a higher chance of measuring animal presence from a larger distance than the
temperature sensor. So, in that case, a drone camera can be moved to the other
direction to view the animal. That is really helpful to capture the movement
and can also be used to save the drone from larger size animals like whales. The
pressure sensor not only works as a pressure sensor. It also works as a
temperature sensor too. The usage of two temperature sensors helps to minimize
the error by getting two readings.
Lights
There are two
led lights are attached to the drone at the front. These lights help to clear
the darkness coming in the camera. The lights give the proper view to the
camera and help to capture the best visuals. The led button is present on the
remote. So, in case to turn off the led the button will be helpful. The led and
drone will be fully controlled through
Monitoring
The monitor part
is very helpful for drone movement but it has some specific limitations. In
which the main one is the time delay between camera and screen due to the low
latency rate. So, to operate the drone always keep in mind that it has sensor
values that show on the top of the screen. Always keep an eye on the top of the
screen, that is really helpful.
Drone Body
The
body of the drone is fully optimized according to the water flow and sensor
requirements. The body helps to operate the engine in a smart way. Especially it
helps to make a path in the water and also helps in standing on the water in case
of water. There will be water resistance on the drone but the design of the
body minimizes it in many ways.
WARNINGS
|
|
Don’t
open the drone, unless you have knowledge about its internal structure. It
has been sealed to protect itself from water.
|
|
Don’t
place the drone in hot water the other camera and ultrasonic sensors could be
affected by high temperature
|
|
Keep an eye on the sensor values to operate efficiently.
|
Note: The Drone image and 3d file were taken over the internet just to represent the project.












![Window 10 pastes random hashed string [Solved] Window 10 pastes random hashed string [Solved]](https://1.bp.blogspot.com/-NLMMwdA07UE/YY_v0twlZuI/AAAAAAAAJwE/qEtHnUIiQeQoOF7CeMxz24SyvBVznfWTQCLcBGAsYHQ/w640-h428/computer-virus.jpg)
![Window 10 pastes random hashed string [Solved] Window 10 pastes random hashed string [Solved]](https://1.bp.blogspot.com/-auD7v3sy8EE/YY_tEfuTfmI/AAAAAAAAJv0/Qnkjzln70GgjwV3BFo9PqKM92oXMLJ-sgCLcBGAsYHQ/w640-h360/svhost.jpg)
![Window 10 pastes random hashed string [Solved] Window 10 pastes random hashed string [Solved]](https://1.bp.blogspot.com/-AFWtsWgmADg/YY_t8tX3KCI/AAAAAAAAJv8/oNadHBJLUgESk3Li2XYKqtntSBGQw3gxgCLcBGAsYHQ/w640-h360/logui.jpg)